Connecting hosts to a Nexus 9k Virtual Switch
Lately I have been playing around with these Nexus 9Kv switches a bit and have been connecting Linux VM's to SVI's/Networks that I have configured on the Switches themselves. For this post, I have a single Nexus 9Kv switch that I will be creating an SVI on in order to connect a Linux VM (TinyCore Linux) to. This is a very basic configuration and will only be going through what's required in both VMWare ESXi and the Nexus switch configuration.
In this LAB the Nexus 9kv switch will have an SVI for vlan 3100 configured and an access port configure for the same VLAN. This access VLAN will also be configured on the ESX server for the specific VLAN 3100 and not as a trunk port (I'm still playing around with trunking etc so this might be possible but I haven't labbed that yet). The host VMs network will also need to be configured on he ESX server for the same VLAN.
Normally I would do this configuration in vCenter, however for this example, I've decided to run through the deployment of this direct from my ESXi server. I'm running ESXi 7 on the particular host but the configuration is the same on 8 as well. I do plan on upgrading to 8 for this one at some point but haven't got around to it yet as I need more RAM for my other ESX host to be able to migrate VMs.
Create the Network
First you will need to create the ESX Network for the new VLAN that the server will sit in. To do this log into your ESXi server and navigate to Networking and click Add port group.
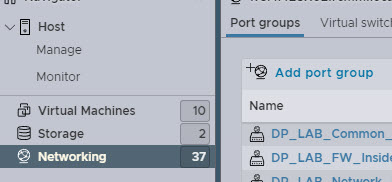
On the Add Port group page, give the port group a name and VLAN ID. You can leave the rest of the information as default and click ADD.
Now that you have your port group, navigate to the VM (If you've already deployed it) by selecting Virtual Machines in the menu on the left.
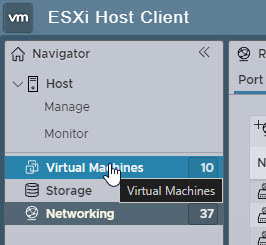
From the list of VM's right click on the VM that you want to connect to your Nexus Virtual Switch and select Edit Settings
Under the Network Adapter 1 drop down, select the new network that you created in the previous step and click Save
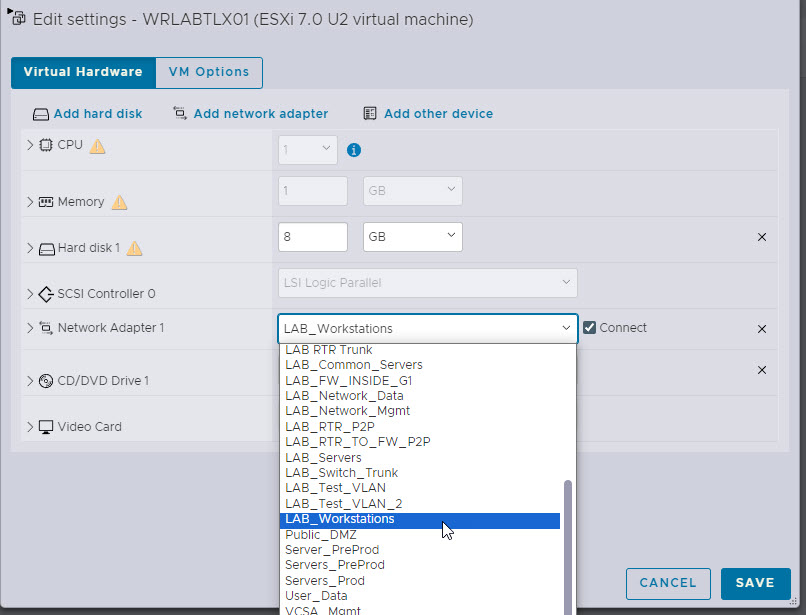
Now you will need to configure the port on the Nexus VM. I've specified to use a new interface and an access port in VLAN 3100. To add the network port right click on your virtual switch VM and select Edit Settings.
Select the drop down list for the correct interface that you are going to configure. Remember here that Network Adapter 1 is always the management interface and Network Adapter 2 starts at Eth1/1 for the device switch ports so in my Lab I'll be configuring Eth1/5.
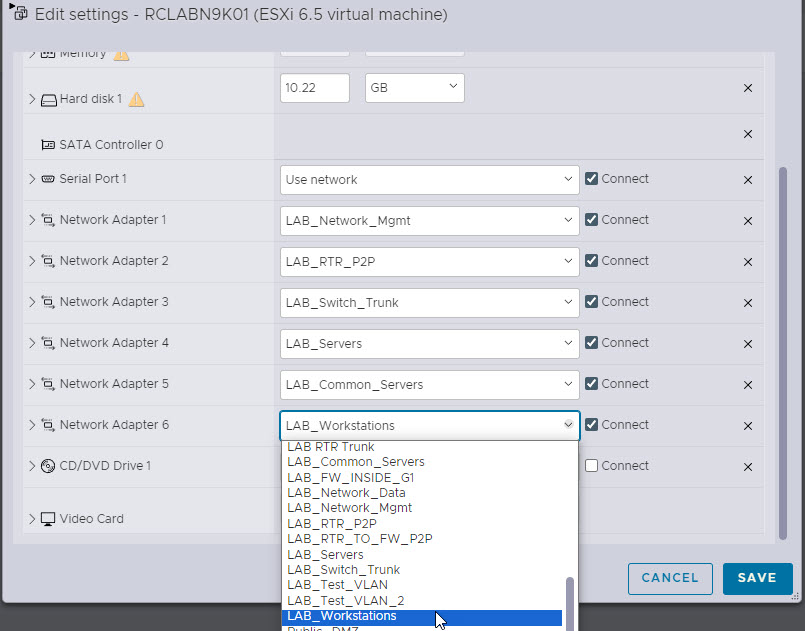
Configure the Nexus Virtual Switch Port
Now that you have the networks and adapters configured, make sure to take note of the VM Network Adapter MAC address of the port you will be using. To view the VM MAC address expand the Network Adapter section.
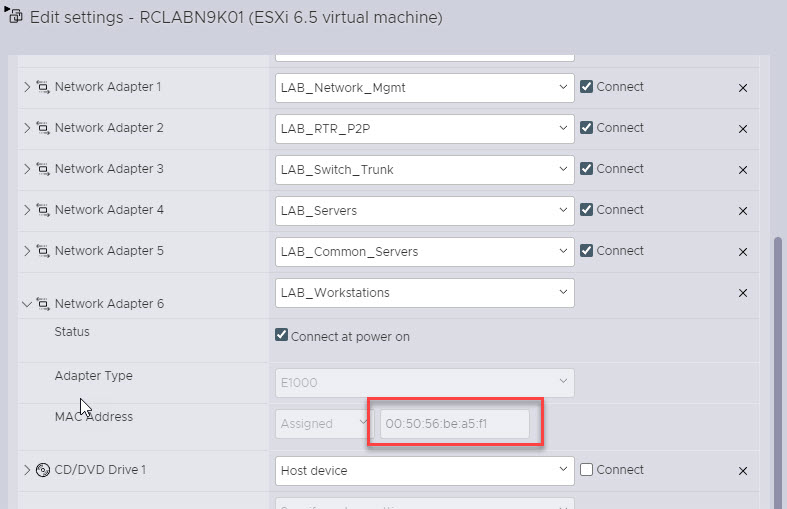
Once you have all the information required, it's time to configure the switch itself. To do that, SSH into your Nexus Switch and create the VLAN, configure the specified port in the access VLAN, and then create the SVI. Make sure that when you configure the SVI, you also configure the MAC address as the one from the VM Adapter.
vlan 3100
name LAB_Workstations
interface Ethernet1/5
description LAB Workstations - VLAN 3100
switchport access vlan 3100
interface Vlan3100
description LAB Workstations
no shutdown
mac-address 0050.56be.a5f1
ip address 10.199.100.1/24
Confirm Network Connectivity
With that done, it's time to configure the VM host. In my case I've created a Tiny Linux VM. I chose this because it's so lightweight and all I need it for is reachability testing. I've configured the Linux VM to have an IP address of 10.199.100.10.
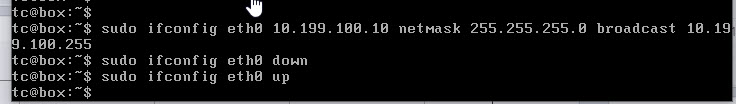
sudo ifconfig eth0 10.199.100.10 netmask 255.255.255.0 broadcast 10.199.100.255
sudo ifconfig eth0 down
sudo ifconfig eth0 up
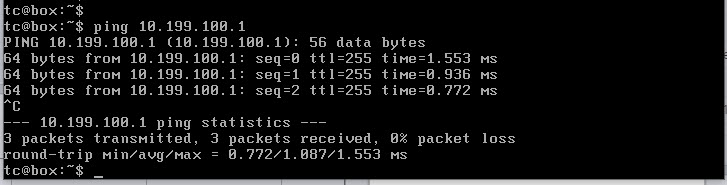
With the VM network configured, it's not time to test connectivity by pinging the Nexus Switch SVI that we created.
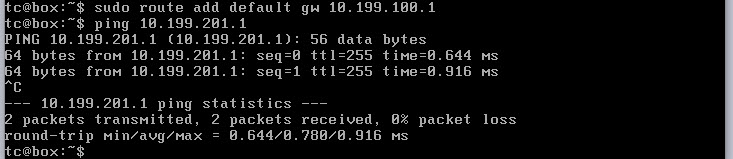
In order to get access to networks outside the 10.199.100.0/24 subnet I have added a default gateway to my TinyCore VM..
sudo route add default gw 10.199.100.1
With that added I can now ping outside of the 10.199.100.0/24 subnet.
And that's it. You should now have a working SVI on your virtual switch and be able to use it as the gateway for another VM or any physical device for that matter. If you've noticed anything missing or have any issues with this post, please leave a comment and let me know.

Add new comment