Sending ISE Radius logs for Palo Alto User-ID
If you've read my recent posts, you'll know that I have a PA-220 firewall in my home lab now and have setup wired and wireless 802.1x authentication in my home network using Cisco ISE. I've now decided that I'd like to make use of the PA User-ID feature in my home network to allow only authenticated users access to specific resources on the network. To do this, I'm going to use the Cisco ISE Radius Accounting logs to send the user information to the firewall and create rules based on username instead of source IP. This makes it easier to allow access from specific sources when using DHCP without having to configure static DHCP reservations. For this post, I'm using Cisco ISE 3.2, and the PA-220 is running a 10.2 release.
To start with, I'll begin by making the necessary changes in Cisco ISE. To send the Radius Accounting logs to the PA firewall, you'll first need to create the Remote Logging target. Log into your Cisco ISE server and navigate to Administration -> System -> Logging.
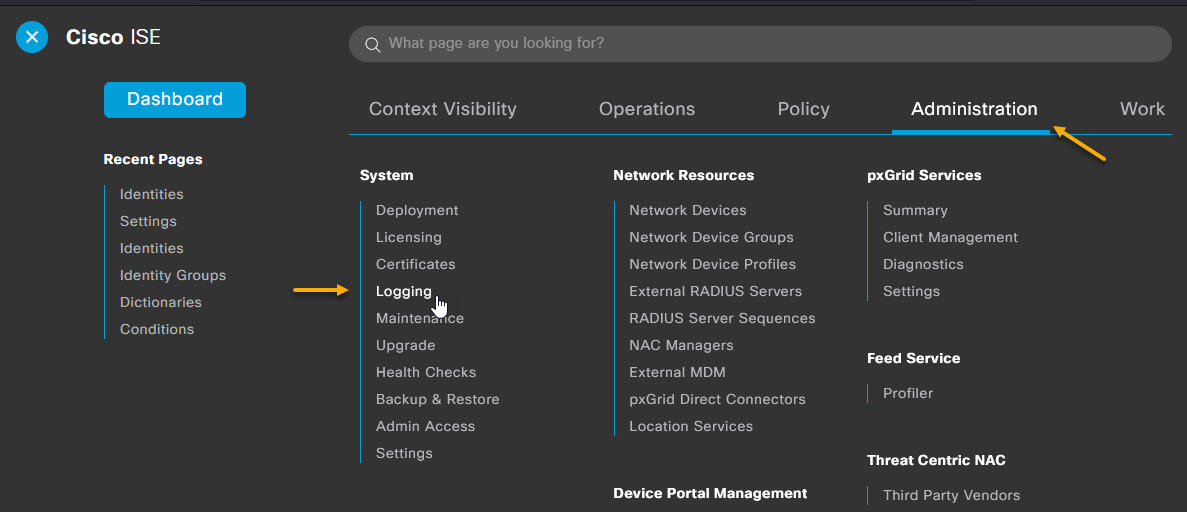
Select Remote Logging Targets from the menu on the left, and click +Add.
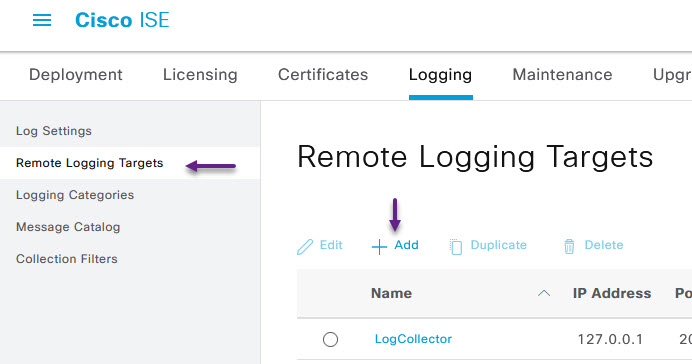
On the Logging Target page, enter the PA firewall IP in the Host/IP address section and fill in all of the other information and click Submit. The IP to specify here is the IP of the interface that will receive the User-ID Syslogs. If you're using UDP for the Syslog target type, you'll receive an are you sure message when you click OK, click Yes on this and continue.
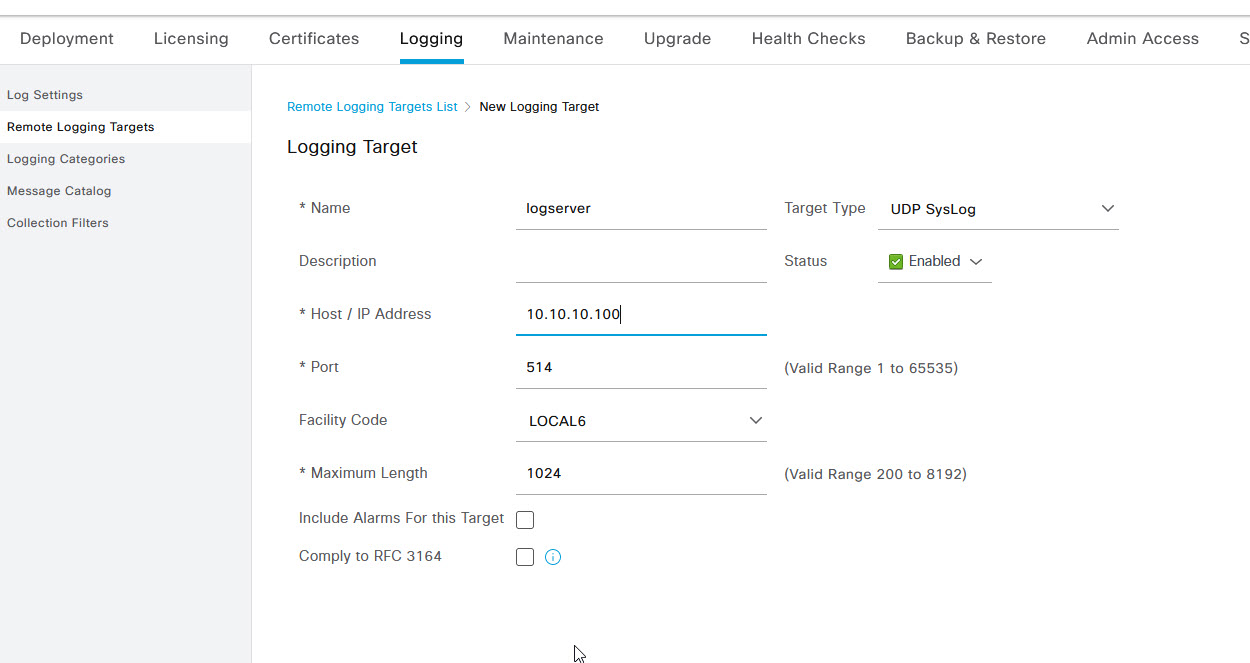
Once you've configured the logging server, back on the logging page, select Logging Categories, and then select RADIUS Accounting and click Edit
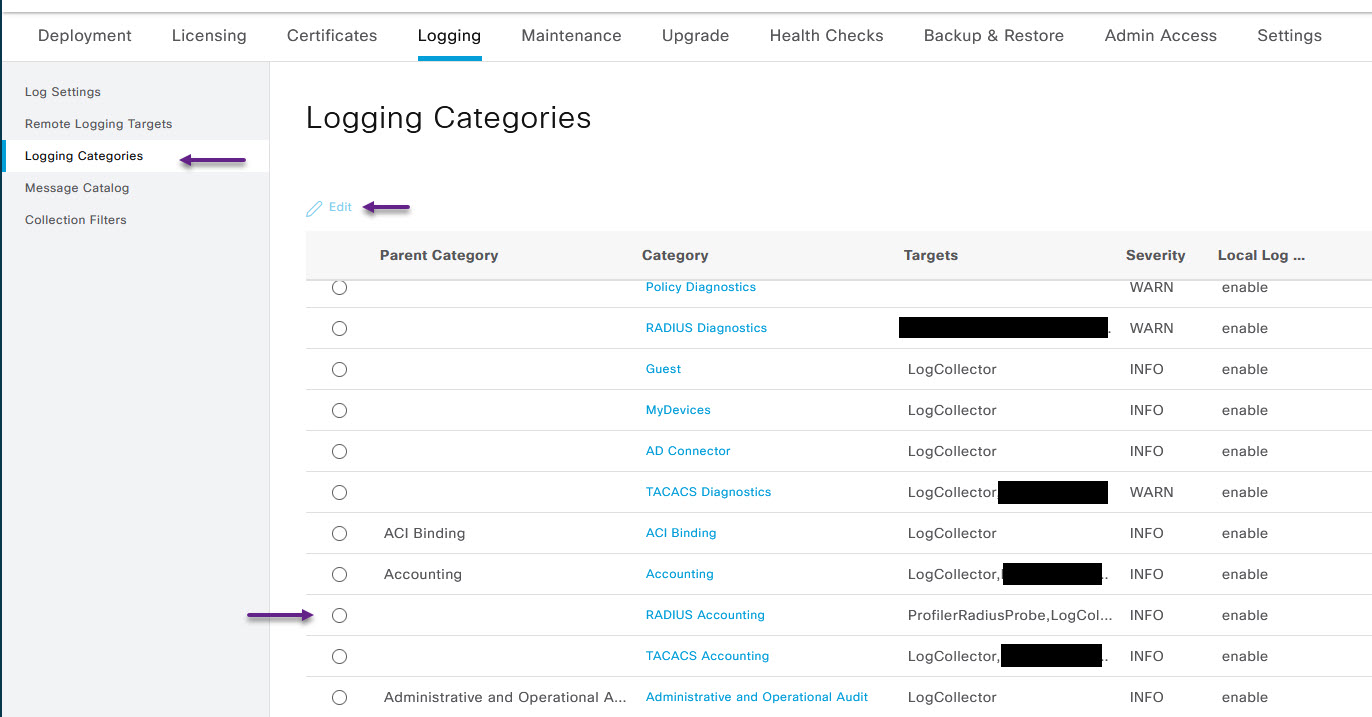
On the Logging Category page for Radius Accounting, select the remote logging server, and click the > button to add it to the list. Once that's done, click Save.

That's it for the Cisco ISE configuration, now you will need to configure the PA firewall to receive those syslog messages and tell it what information to filter for. To do that you will first need to create a Syslog Filter for the Radius Accounting logs. Navigate to Device -> User Identification -> User Mapping and under the Palo Alto Networks User-ID Agent Setup section, click the cog to edit.
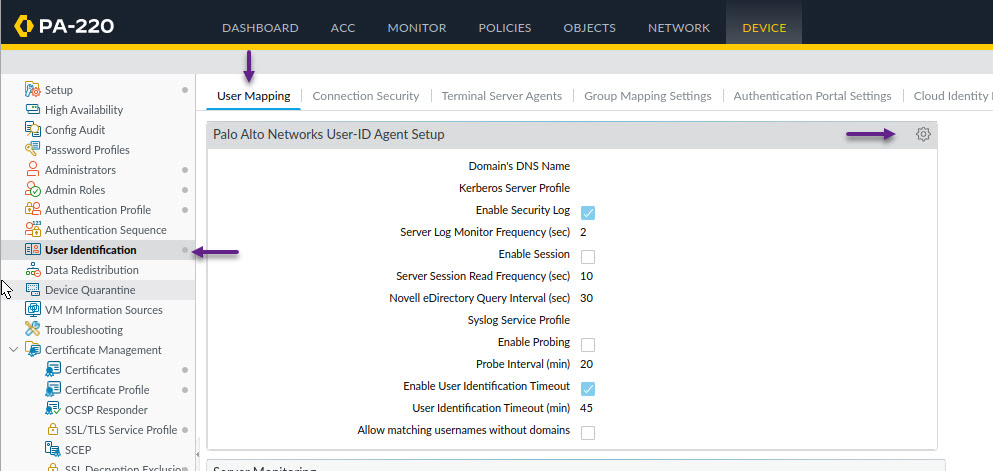
In the User-ID Agent Setup window, select Syslog Filters and click Add
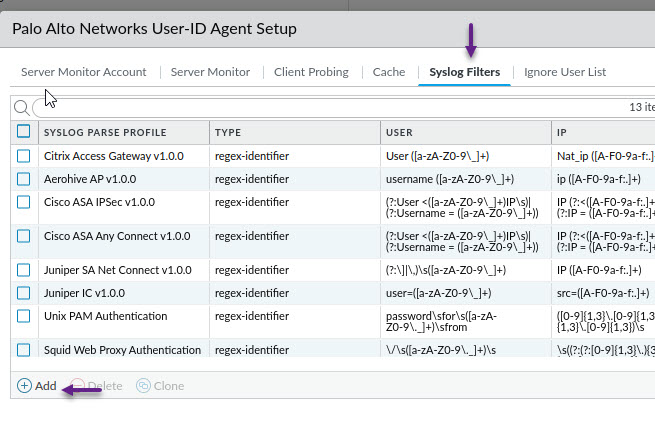
This is where you need to enter very specific information in order to match and parse the syslog entries sent from ISE. Give the profile a name and a description and select the Type as Field Identifier. Enter the following information in each field exactly as is. Once done, click OK.
Event String: NOTICE Radius-Accounting: RADIUS Accounting
Username Prefix: User-Name=
Username Delimiter: ,/s
Address Prefix: Framed-IP-Address=
Address Delimiter: ,/s
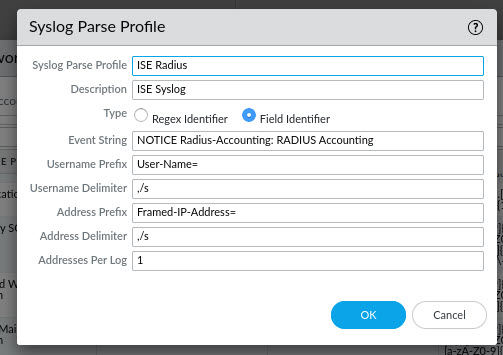
With the filter profile configured, now you can configure the Server settings. Under the Server Monitoring section, click Add.
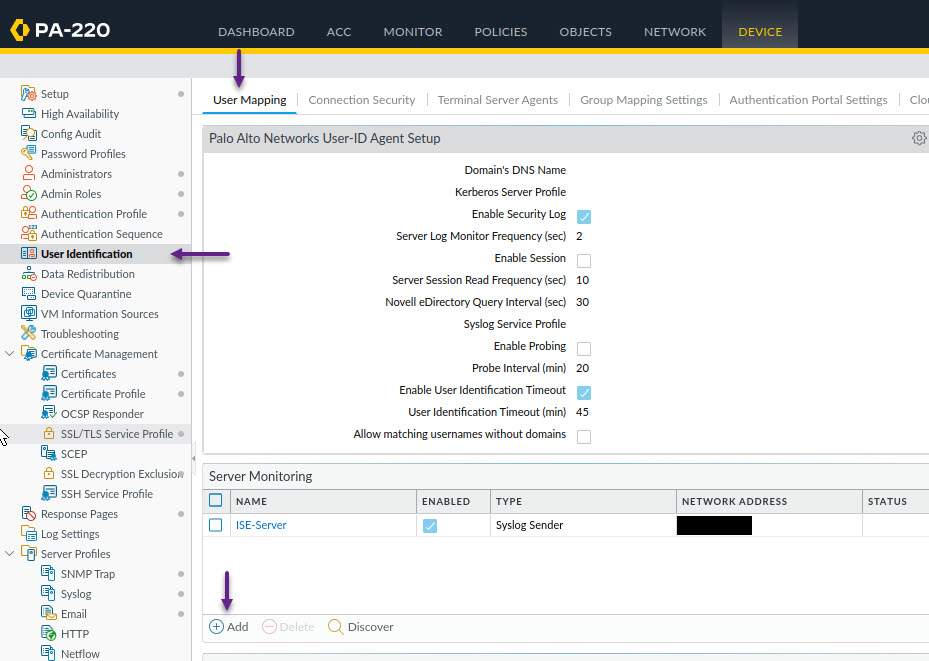
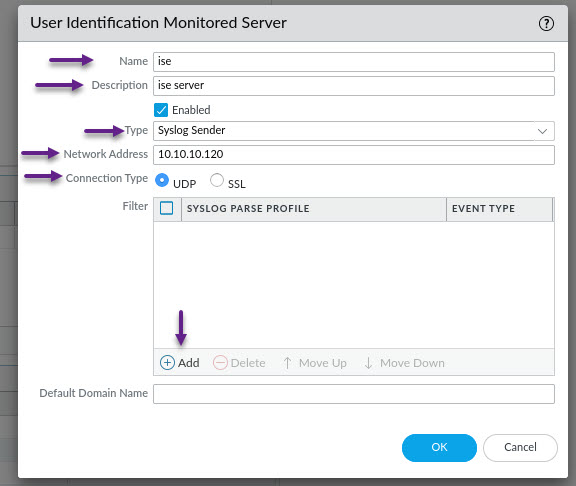
In the User Identification Monitored Server window, enter the Cisco ISE server details and set the type to Syslog Sender. In the Syslog Parse Profile section, click Add and select the ISE-Radius profile that you created earlier from the options menu. Once done, click OK. This step will need to be done for each ISE PSN in the deployment that will send User-ID Syslog Messages.
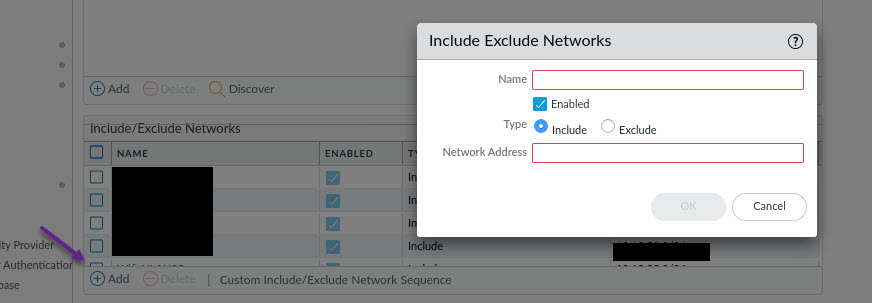
If you want to include or exclude specific subnets of your network to grab User-ID information, under the Include/Exclude Networks section on the User Mapping page, you can click Add and add in each subnet to match user-id's against. Once done, click OK.
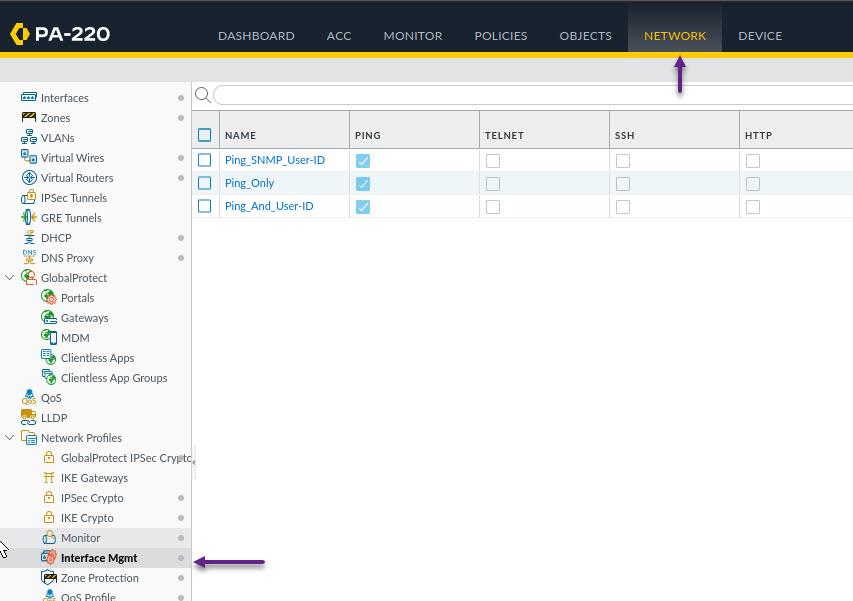
That it for the User-ID mapping configuration. Now you will need to configure the PA Firewall interface to allow User-ID information via syslog. To do that, you will need to configure a management profile. Navigate to Network -> Network Profiles -> Interface Mgmt.
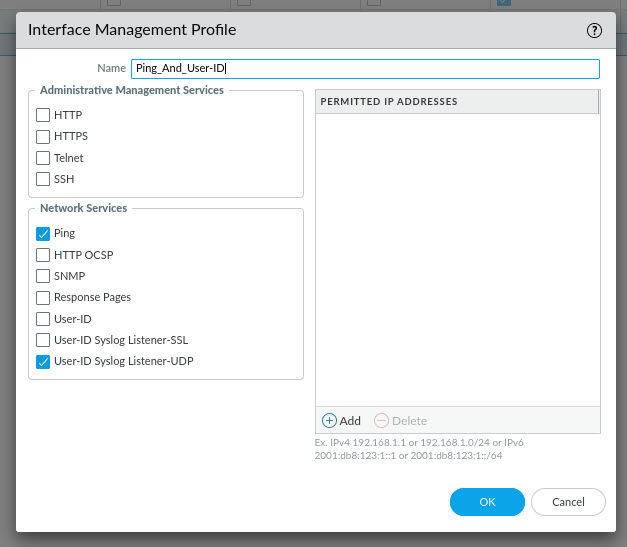
As you can see, I already have a few profiles configured and if you have one already, you can simply select the profile to edit it. If not, click the Add button at the bottom of the page. In the Profile settings window, give the profile a name and select the services that are to be allowed on the Interface. For this profile, i'm allowing Ping, and User-ID Syslog Listener-UDP only. You can also restrict the access further but specifying IP address/subnets in the permitted IP Address space field and include only the IP of the ISE server and any device that should be able to ping the specified Interfaces. Once you're done, click OK.
Now you will need to assign that profile to an interface. The Interface will be the same one that you configured as the Target for the Cisco ISE Radius Accounting logs. To do that, navigate to Network -> Interfaces and select the correct interface to edit the settings.
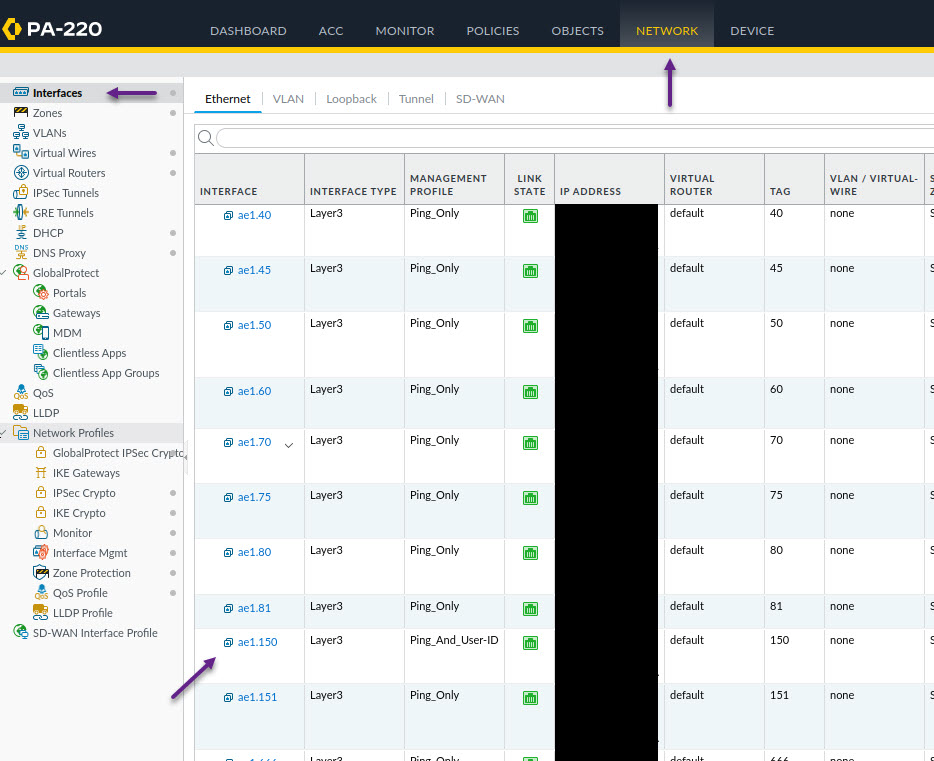
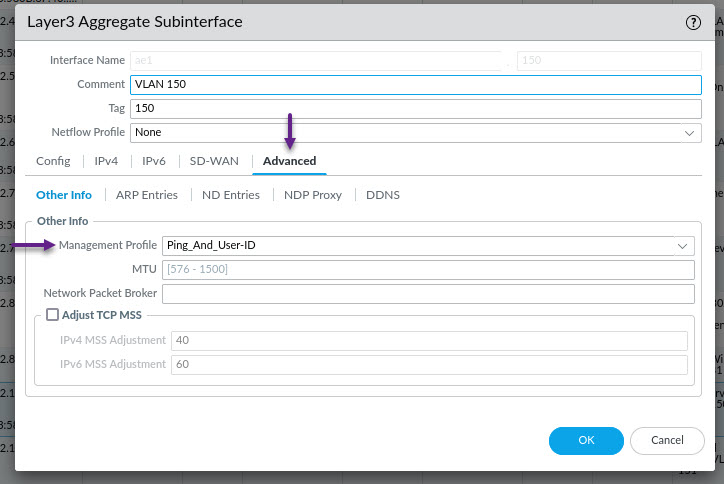
On the Interface Settings page, click on the Advanced tab, and in the Management Profile drop down, select the profile you created in the previous steps. Once done, click OK.
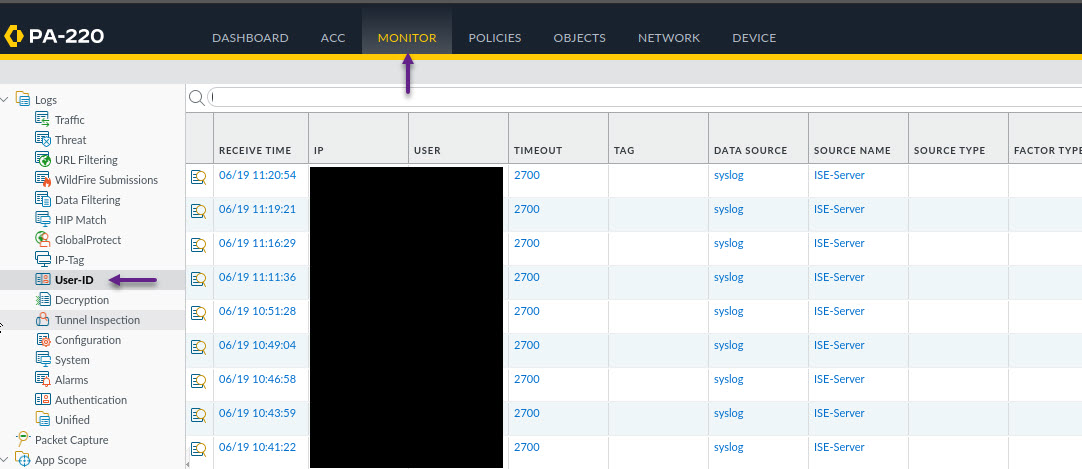
And that's it. Now you can commit the changes to your Firewall and start creating rules based on User-ID. Once the changes are committed, you can verify User-ID logs are being received on the Monitor page. Navigate to Monitor -> User-ID to verify the User-ID log information.
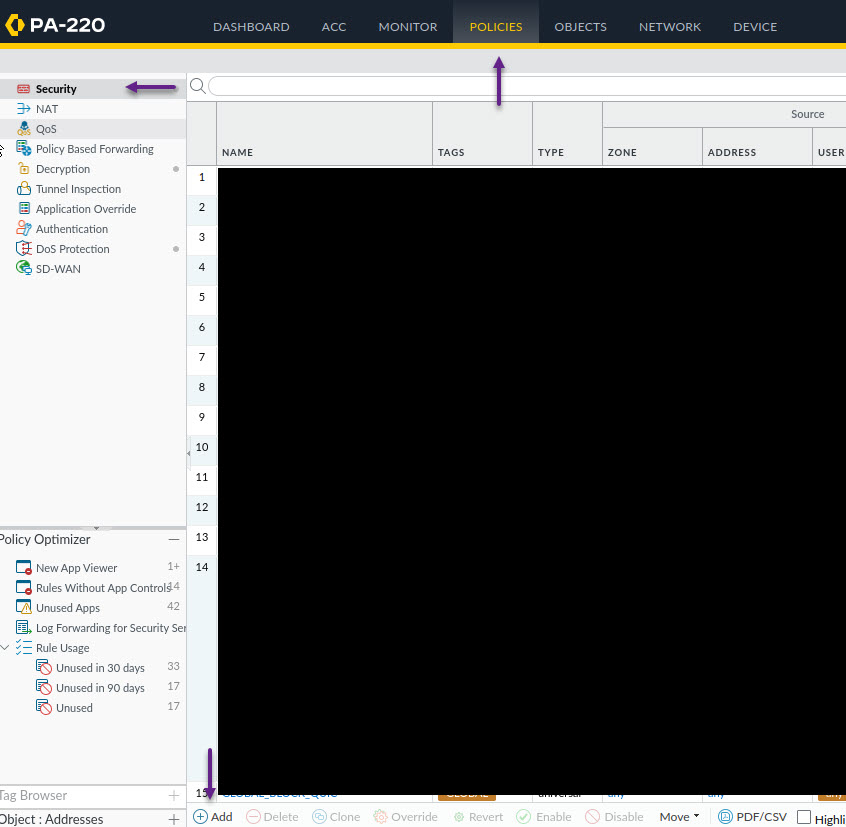
There are other timeout settings and if you have AD groups, group settings that can be configured, but that's the basics of it and I don't have an LDAP/AD server to choose groups from etc. The next step is to create a rule for your users. To do that, navigate to Policies -> Security and click Add to create a new rule.
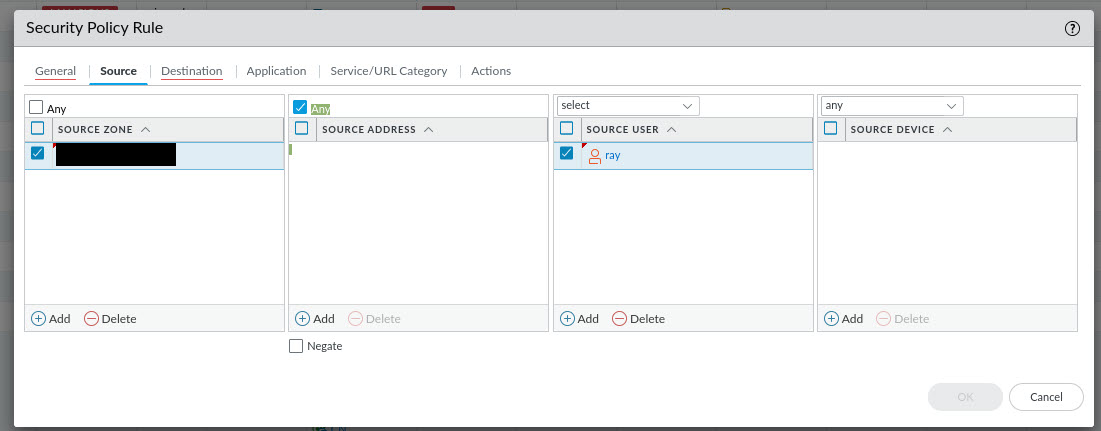
Fill in all of the required details to create your rule but on the Source tab, you will see an option for Source User. In this field, click Add, and enter the username (Or Group if you have AD/LDAP configured) that you want to allow for this rule. Once you've finished with the rule details, click OK and then commit the changes.
That's it for this post. You should now be able to receive and parse Radius Accounting logs from Cisco ISE on your PA firewall to obtain user-id to IP address mapping information. If you've noticed anything missing or have any issues with this post, please leave a comment and let me know.
Comments
Any possibility to do this via pxGrid ?
Hello ray,
Thanks for this detailed procedure !
Do you happen to know if there is any possibility to do the exact same thing using pxGrid instead of syslogs ?
In my case, an end-user authenticates on a guest portal hosted by ISE and I would like to have the username/IP couple transferred to Panorama via (an already established) pxGrid link, so I can reuse this information in authenticated firewall rules (source IP + source user).
Thanks,
Best regards
Thanks for the comment. I…
In reply to Any possibility to do this via pxGrid ? by Hlx (not verified)
Thanks for the comment. I haven't setup anything with pxGrid myself but your comment has me curious. When I get some spare time i'll dig into it a bit an find out but i don't know if the filtering will work, it would depend on the information in the syslog message.

Add new comment