Palo Alto LACP HA Passive configuration
This post will go through configuring a Palo Alto firewall HA pair using LACP and enabling HA Passive State to speed up failover.
I was looking into the fail over process on Palo Alto firewalls when configured in and active/standby configuration and having ports in LACP mode and was testing some failover procedures and found that without enabling specific LACP fail over settings there was noticeable packet loss while LACP negotiated on the standby PA.
Using LACP on a PA, or any device for that matter allows you to bundle multiple physical ports together into a single logical interface. This allows for greater overall bandwidth over a single interface on a per flow basis based on your port channel algorithm. Obviously this design decision makes sense but what happens with LACP port negotiation on the passive device when in a HA Active/Standby pair? Well turns out Palo Alto have thought of that, and have a feature called HA Passive State for LACP. What this does is causes the passive firewall to have it's interfaces up and already enabled and configured in the port-channel. This allows for faster transition when failing over as the ports don't need to come up and then have LACP negotiate and the port channel come online and in my testing, it did exactly that. I lost 1 to 2 pings when failing over with this feature enabled.
While there's plenty of documentation out there on how to enable this on the PA, I decided to do a post about because there was a caveat when it came to configuring the switch ports so to save others from having to waste time googling and playing around, I figured why not write it up here and hopefully help someone else out.
To configure an aggregate interface on a PA, navigate to Networks -> Interfaces and click Add Aggregate Group.
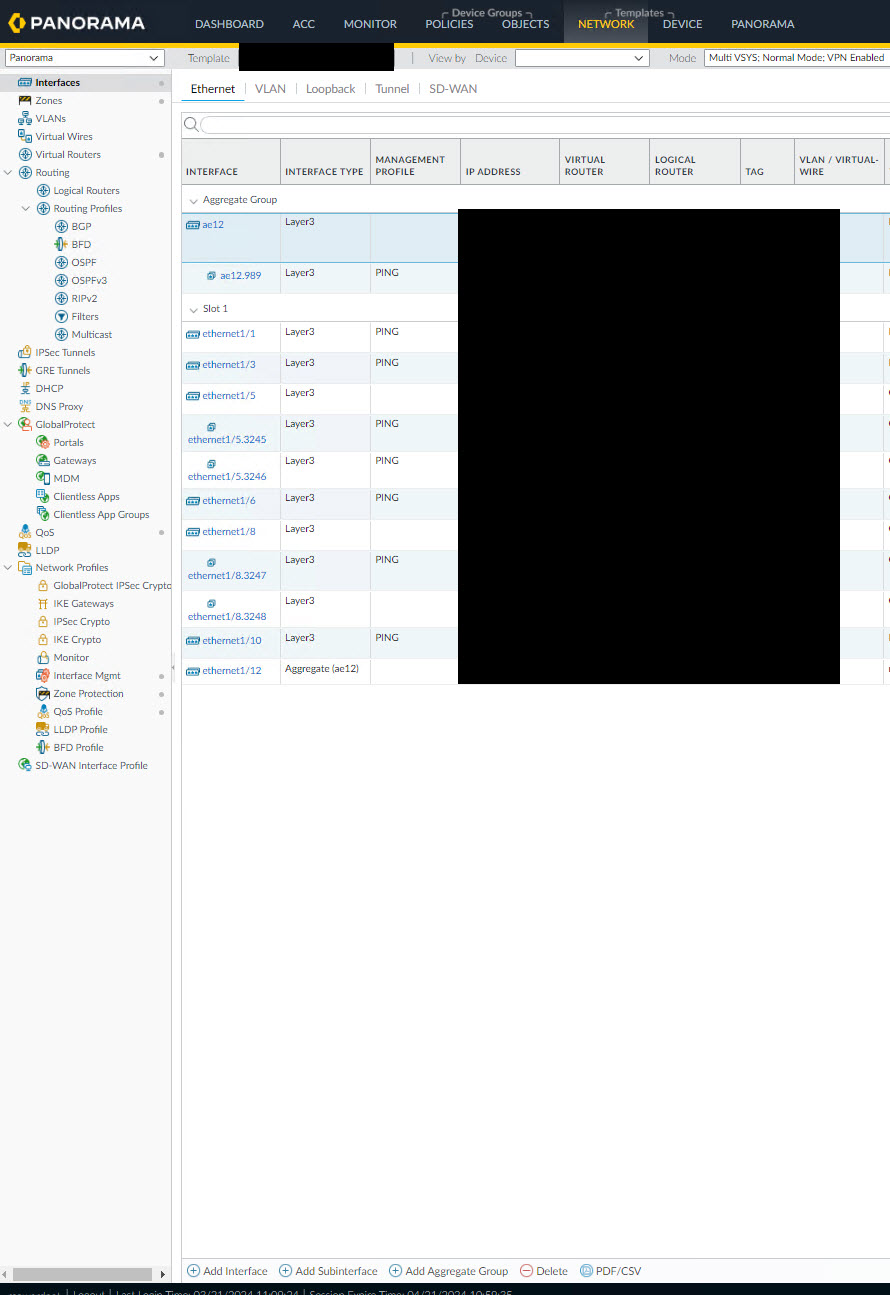
On the Aggregate Ethernet Interface settings popup, select the LACP tab and enable LACP. You can choose to leave all of the settings as defaults or you can alter them to suit your environment but the key option here is the High Availability Options. Make sure to select Enable in HA Passive State. Once done, click OK.
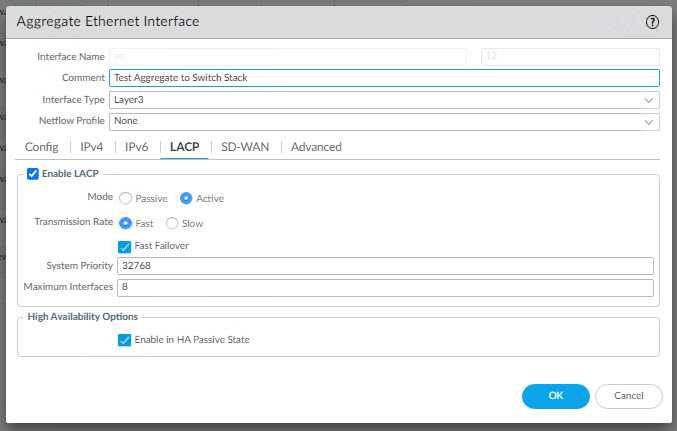
Now you can configure an Aggregate Sub Interface. On the Interfaces page, select the Aggregate interface you created in the previous step and then select Add Sub interface.
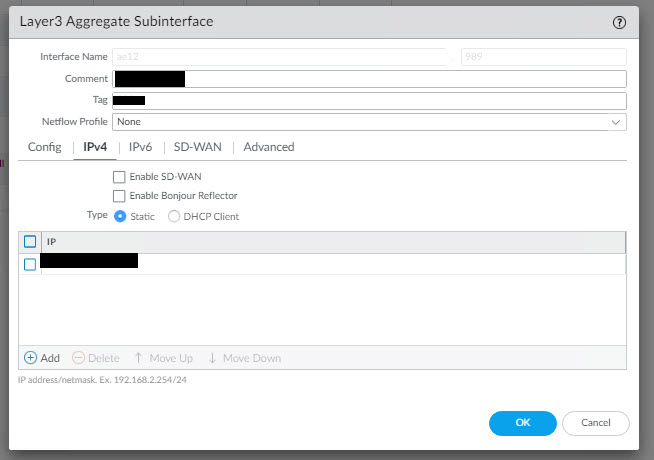
Configure all of your sub interface information such as IP, VLAN tag, Virtual Router, Zone etc And one done, click OK.
When you enable LACP in HA Passive state, you will also need to ensure that you have configure the PA HA link state. To do that navigate to Device -> High Availability.
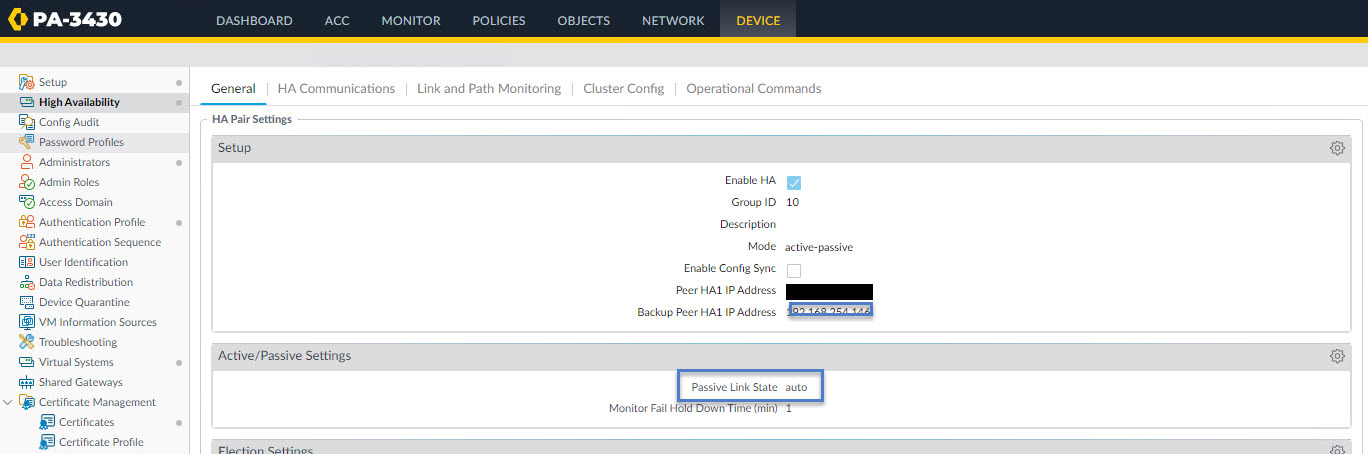
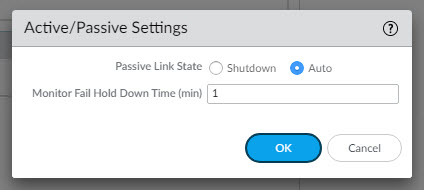
To change click cog and select auto and click ok
Now to configure the switch. I'm using a catalyst 9k switch in this test and this is where the caveat comes in. For the switch configuration you must ensure that the active and the standby device are in separate port-channel's instead of bundled in the same port channel. For this configuration I've used Port-channel 20 for the active and port-channel 21 for the passive firewall.
Active firewall port 1
interface TwentyFiveGigE1/0/20
description Test LACP TO FW
switchport mode trunk
storm-control broadcast level 0.30
storm-control multicast level 0.30
channel-group 20 mode active
spanning-tree portfast networkPassive firewall port 1
interface TwentyFiveGigE2/0/20
description Test LACP TO FW
switchport mode trunk
storm-control broadcast level 0.30
storm-control multicast level 0.30
channel-group 21 mode active
spanning-tree portfast networkBelow is the port-channel interface configurationfoe port-channel 20 and 21.
interface Port-channel20
description Test LACP TO FW
switchport mode trunk
storm-control broadcast level 0.30
storm-control multicast level 0.30
interface Port-channel21
description Test LACP TO FW
switchport mode trunk
storm-control broadcast level 0.30
storm-control multicast level 0.30Once the port-channel's are configured and LACP is enabled on the firewall you can verify the port channel status on the switch using the command show ether channel summary. Note that this command could differ depending on yhr platform you're using and the IOS version.
SWITCH-STACK#sh etherch sum
Flags: D - down P - bundled in port-channel
I - stand-alone s - suspended
H - Hot-standby (LACP only)
R - Layer3 S - Layer2
U - in use f - failed to allocate aggregator
M - not in use, minimum links not met
u - unsuitable for bundling
w - waiting to be aggregated
d - default port
A - formed by Auto LAG
Number of channel-groups in use: 6
Number of aggregators: 6
Group Port-channel Protocol Ports
------+-------------+-----------+-----------------------------------------------
20 Po20(SU) LACP Twe1/0/20(P)
21 Po21(SU) LACP Twe2/0/20(P) Failing to configure the active and standby device in separate port-channel groups will result in the passive device ports being put in a suspended state as they can't properly negotiate LACP.
SWITCH-STACKJ#sh etherc
*Mar 22 00:58:00.653: %SYS-5-CONFIG_I: Configured from console by ray on vty0 (10. 1.1.1) sum
Flags: D - down P - bundled in port-channel
I - stand-alone s - suspended
H - Hot-standby (LACP only)
R - Layer3 S - Layer2
U - in use f - failed to allocate aggregator
M - not in use, minimum links not met
u - unsuitable for bundling
w - waiting to be aggregated
d - default port
A - formed by Auto LAG
Number of channel-groups in use: 5
Number of aggregators: 5
Group Port-channel Protocol Ports
------+-------------+-----------+-----------------------------------------------
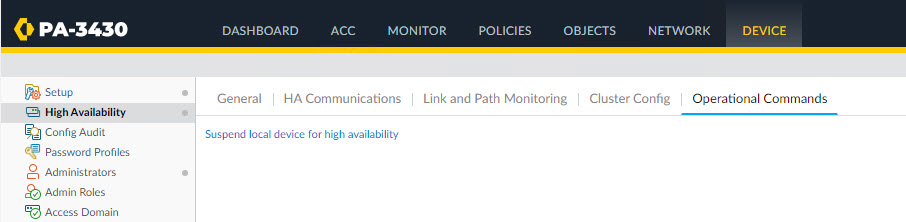
20 Po20(SU) LACP Twe1/0/20(P) Twe2/0/20(s) With all the port-channels configured and the firewall done, it's time to test the fail over. To so this I ran a continuous ping from the switch and then triggered a fail over on the firewalls. To trigger a fialover on the PA, navigate to Device -> High Avalability -> Operational Commands and click on the Suspend local device for high availability link.
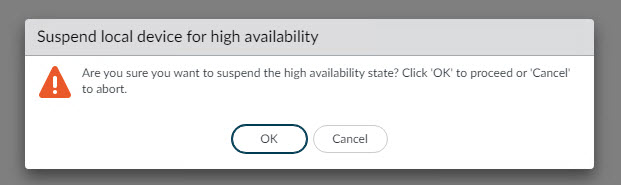
Click OK when prompted to trigger the fail over.
As you can see below in the ping results, once the fail over had been triggered, 2 pings were lost and then reachability was restored.
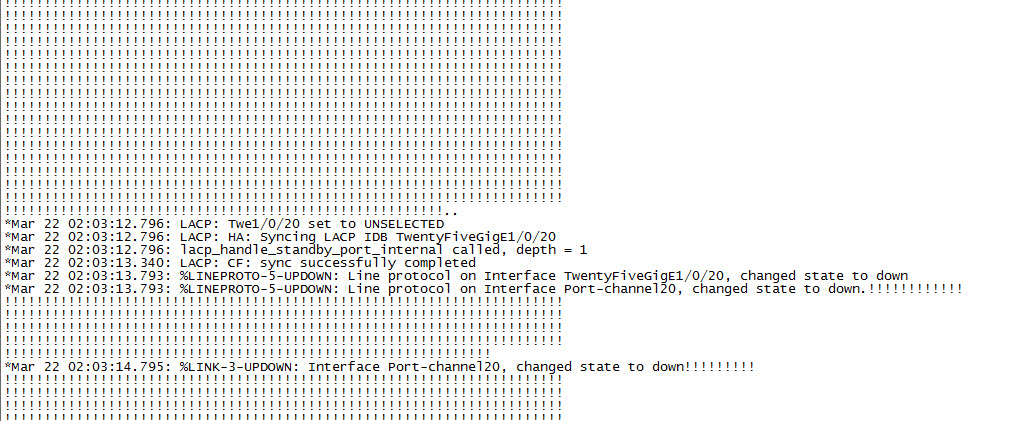
And that's it for today's post on PA LACP fail over. If you've noticed anything missing of have any issues with this post, please leave a commend and let me know. If you've noticed anything missing of have any issues with this post, please leave a commend and let me know.

Add new comment