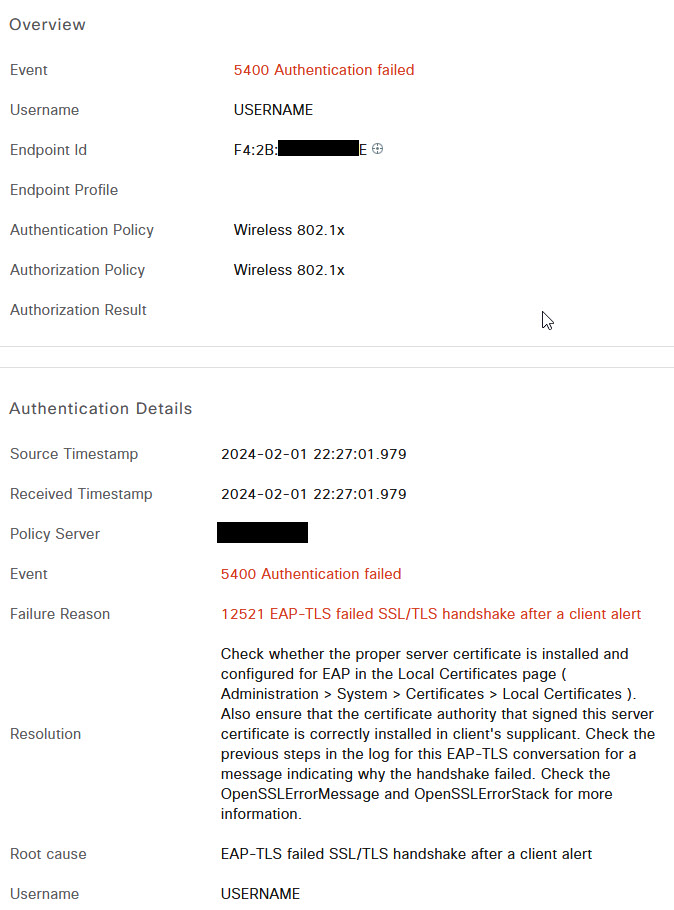
Kali Linux login boot loop
I've been playing around with Kali Linux lately and trying some of the basic tools for pen testing. Not for anything in particular other than my own curiosity and several times i found that when I connected to the VM Console or attempted to VNC to the server, I would enter my credentials and it would appear to login, but then simply present me the login screen again. No matter how many times i tried, I was not able to actually log in to the server.